Magento Security Scanner to Find Vulnerabilities & Malware
- November 13, 2024
- Posted by:
- Category: Uncategorized
According to website security solutions provider Astra, all e-commerce platforms, including Magento, have vulnerabilities.
As a result, 62% of e-commerce stores have had at least one exposure to malware, and 60% of stores have an SWF (or small web format) uploader open vulnerability.
Even with the increasing number of security breaches, 49% of Magento e-commerce portals do not use SSL certificates, and small and medium-sized businesses are especially vulnerable.
An e-commerce store cannot muscle past a data breach easily. A single breach can cost as much as $117,000, and 60% of businesses never recover from an incident.
The cost of a data breach is increasing by the month. How then does an e-commerce business adopt a fool-proof security system that can withstand an intrusion attempt? The answer lies in a robust e-commerce security scanner.
If you own a Magento e-commerce website, you could turn to Magento Security Scan offered by Adobe and specifically designed for the needs of Magento users.
What is Magento Security Scan?
Magento Security Scan is a free tool that proactively detects malware on a website. Business owners and developers can access it by creating an account on the Magento website.
The Magento Security Scan is a web-based tool that is regularly updated by Adobe and does not need installation.
To identify vulnerabilities, the Magento scanner runs over 30 tests and locates missing Magento patches, configuration issues, and others.
The e-commerce security scan can be scheduled to run daily or weekly, and the report on security risks, malware, and unauthorized access is emailed to the site admin.
The tool can be found in the Magento Security Center and is compatible with Magento Community and Enterprise editions.
Here are some of the key benefits of the Magento Security Scan
- Real-time insights into the security status of the Magento website.
- Access to a host of best practices and suggestions to address existing vulnerabilities.
- Access to a large cache of security tests to identify potential malware on a site’s security system.
- Historical reports to monitor and track the progress of the security status of the site over time.
- Details of successful and failed checks, with a list of actions required.
- Option to schedule the security scan to run daily, weekly, or on-demand.
- Easily fix potential vulnerabilities and adopt a schedule to update malware patches.
- Adobe accords high priority to security. For instance, Magento 2.4.2, has received over 35 security enhancements. These patches address several vulnerabilities, including remote code execution and cross-site scripting (XSS).
However, cybercriminals search for and identify new vulnerabilities all the time and an e-commerce site should ensure its security is always updated and take preemptive action.
What are the Different Security Threats to Your Magento Store
There are a host of security threats to a Magento e-commerce store, below is a list of a few and ways to address them with a robust Magento scanner.
DDoS
A Distributed Denial of Service or DDoS attack is a malicious attempt to disrupt the normal traffic of a website by overwhelming it with a flood of internet traffic. This traffic often comes from other compromised devices and can cause a site to crash.
A DDoS attack can be from a single source which is easier to deal with or from complex and adaptive multi-vectors. A DDoS can be of various types, namely, volume, protocol, and application based.
A multi-vector DDoS overwhelms a target website in several ways and makes mitigation efforts in any one direction difficult.
A site is under attack when it becomes extremely slow or unresponsive, the problem persists even when the webserver is restarted, and the server logs are overrun with massive amounts of activity.
One way to reduce the risk of a DDoS is to avoid custom or self-hosting your e-commerce site and adopt a Magento malware removal solution.
Ransomware
Ransomware is a type of malware that prevents users from accessing their website and the data on it. The data is usually stolen, deleted, or encrypted and the user receives a ransom request to return their data.
Some of the prominent ways hackers gain access to a company website are through phishing emails or remote desktop protocol (RDP). Typically, the desktop displays the ransom message.
Some ways to prevent a ransomware attack are to create awareness within the organization about clicking on unknown emails, taking continuous data backups, deploying a robust anti-ransomware solution, ensuring security patches are always updated, and adopting user authentication.
Phishing
Phishing can be of various types, such as email phishing or spear phishing where a single enterprise is targeted.
Phishing is a type of social engineering used to steal login credentials and credit card details of users.
The person receiving the message or email is duped into clicking on a link that leads to a website that looks legitimate but is fake. Next, users are asked for personal information.
Loss of payment-related information can result in unauthorized purchases, stealing of funds, or identity theft.
Phishing can be avoided through two-factor authentication and a company-wide firewall.
E-skimming
It is the process by which fraudsters create a replica of an e-commerce site and drive customers to it, installing malware on an e-commerce site and stealing payment and other data while customers are making a purchase, or by sending phishing emails.
E-skimming can be avoided by ensuring security on the site is always updated, adding a robust firewall, and heightening security awareness among employees and customers.
Brute force
It is a method of hacking an e-commerce site by guessing its password. A business knows they have been a victim of a brute force attack when they notice repetitive successive attempts of trying various password combinations from a public IP.
The hackers may also use bots installed maliciously on other computers to boost the computing power required to run such an attack.
A way to protect against brute force attacks is to put in place systems that track excessive requests from a public IP and blacklist it.
The website admin is notified about these brute-force requests and can protect specific endpoints (URLs) from excessive requests.
The simplest way to fend off a brute force attack is to have a strong password with alphanumerics and special characters, ensure the password is changed periodically, and limit the number of login attempts. The site can also use Captcha and two-factor authentication.
Now that we know how hackers can attack e-commerce sites, the next step is to identify ways to shore up the protective barrier.
Below is a list of Magento security scanners that can be deployed to identify vulnerabilities and continuously scan a site for malware.
A short list of #Magento security scanners for finding vulnerabilities and malware
Several different types of Magento security checks available in the market can help an e-commerce business uncover a vulnerability or malware. Here are a few,
- MageReport: is a well-known scanner used to check Magento sites for known security vulnerabilities. It can check for admin disclosure, RCE/webforms vulnerability, visbot malware, API exposure, brute force attacks, ransomware, Gurulnc Javascript, and more.MageReport checks the core Magento and third-party extensions for vulnerabilities. Users can also register at MageReport to get notified of new vulnerabilities when found.
- SUCURI is not specific to Magento but is useful to test a website for various components. It is useful to quickly analyze a site against common online threats such as malware, blacklisting, injected SPAM, and defacements.
- Foregenix tests and provides a high-level report on Magento shoplift, Magmi, outdated versions of applications, unprotected version controls, Cloud Harvester malware, credit card hijack, XSS, RSS attack, secrets leak, and admin takeover/disclosure. Users get instant access to the results, and it is also emailed.
- The Magento Security Patch Tester is designed to help if a Magento store is vulnerable to the latest security risk. It is an ideal tool for quickly verifying the validity of your security patch.
- Acunetix is an enterprise-ready web-based vulnerability scanner that doesn’t slow down the site during a scan. It offers a comprehensive security scan for not just Magento-specific applications but the entire. Scan results include potential resolution, which helps developers and security experts to fix problems quickly. The tool also allows for the generation of PCI, HIPAA, DSS, OWASP, and other reports for compliance officers or business owners.
- The Magento Security Scanner tool is the most popular option for Magento malware removal. Users need to create a free account and verify the site ownership before running the scan.
How to Run a Security Scan in a Magento Store
With security a key concern, here is a step-by-step process on how a business can run the Magento Security Scan on your e-commerce store.
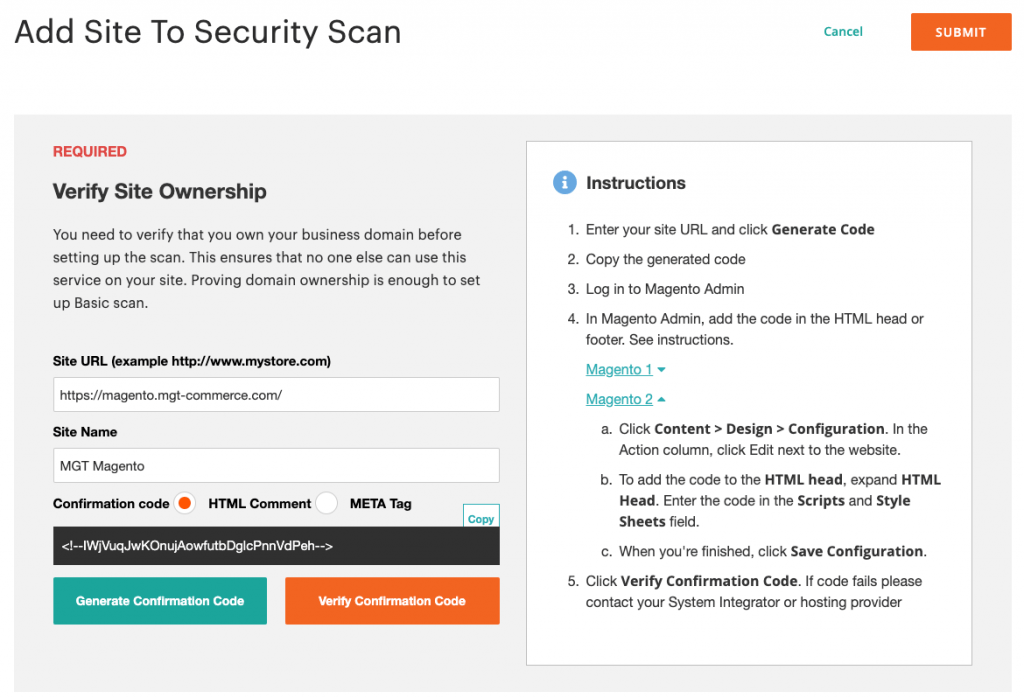
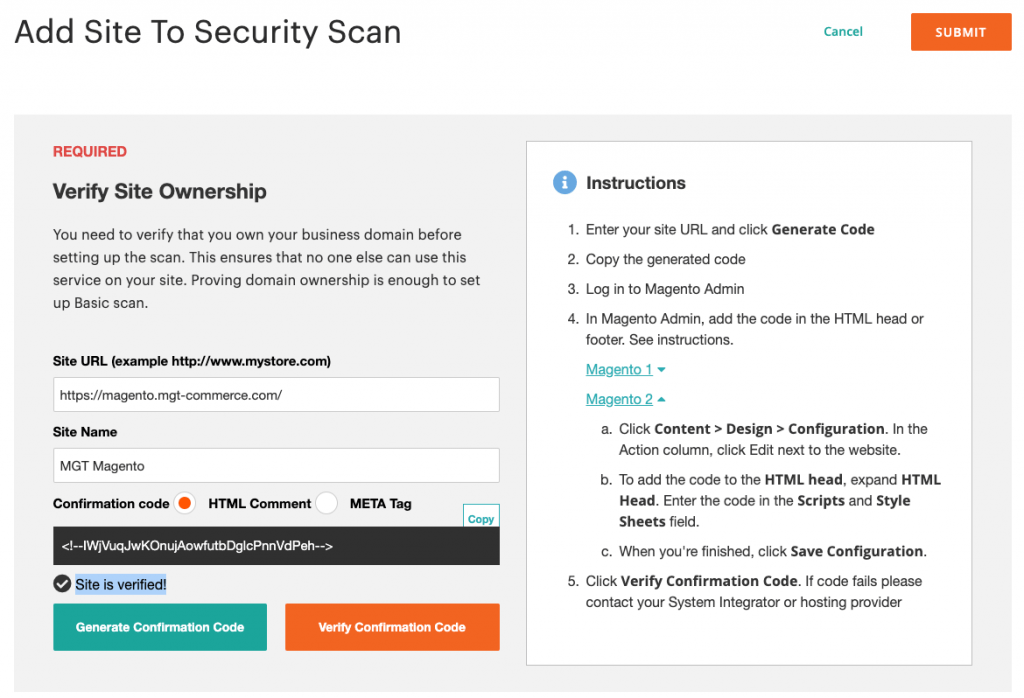
You need to begin by verifying the ownership of your site
Do this by signing in to your Magento account, and following these steps:
- Choose Security Scan and click on Go to Security Scan, seen on the left side of your screen
- Read the Terms and Conditions, and click on Agree
- On the Monitored Websites page, click on the +Add Site button
- Enter your site URL to be scanned, and click on the Generate Confirmation Code option
Your screen will look something like the one below.
The next step is to log in to the Admin of your e-commerce site,
- Click on Content → Design → Configuration in the admin sidebar.
- Next click on your site, Edit option, and expand the section HTML Head on the Scripts and Style Sheets, paste the confirmation code you had copied and click Save Configuration.
- Return to the Security Scan page of your Magento account and click on Verify Confirmation Code.
With this process, you should have verified the ownership of your site.
Configure and schedule the automatic security scan
- After verifying your site’s ownership, the next step is to configure and schedule the automatic security scan. This enables the scan to run automatically weekly or daily.
- Schedule the preferred day of the week, time, and time zone for when to run the security scan. A best practice is to run the scan at night when traffic on the site is minimal.
- By adding an email address, you will receive the results of the scan and service patch announcements. This is a time saver as the user does not need to log in to their Magento account to view the report.
- Click on the Submit button when you are done scheduling the auto scan.
The image below indicates how your screen will look.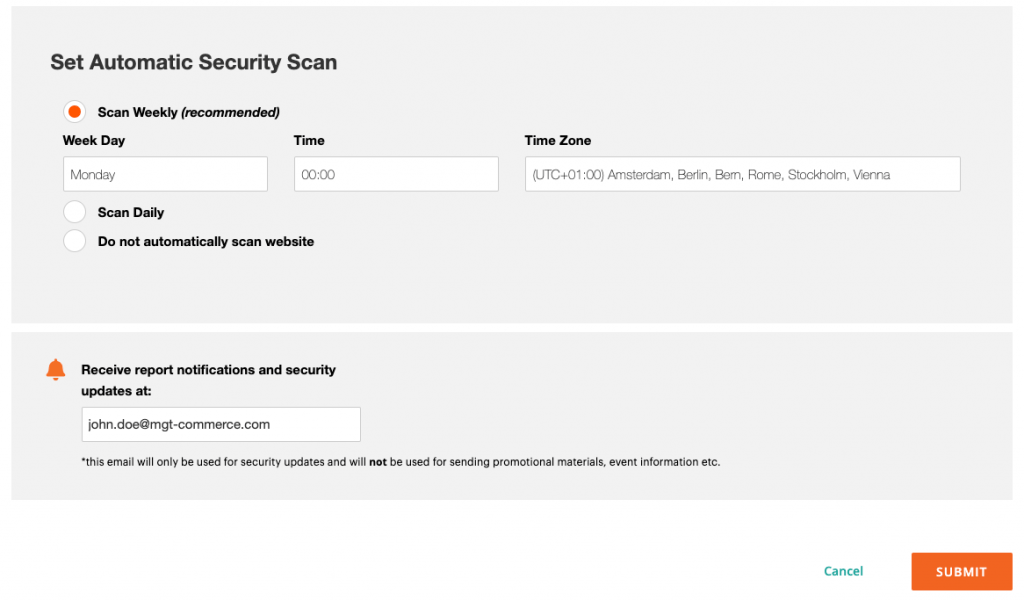
Running the e-commerce security scan manually
If you run the scan manually, you can view the results immediately after the scan is completed. The result is displayed in three tables, namely successful scans, unidentified scans, and failed scans.
Focus your attention on the unidentified and failed scans. Perform the recommended action to improve the security of your e-commerce site. If necessary, get the assistance of an experienced technology partner to ensure the security problems are fixed and safety enhanced.
In conclusion, an e-commerce business can engage in Magento malware removal, but the priority must always be prevention. A scheduled Magento security scan ensures that a website is being scanned at a regular frequency, a cloud-based web application firewall on top of the Magento store can be another level of security.
With the cost of removing malware expensive, prevention is by far the more cost-effective option.
Need help managing the security of your e-commerce website? Navabrind IT Solutions can help.
Navabrind IT Solutions is a full-stack e-commerce technology provider with over a decade of experience in the industry. We manage website security for several clients, and our global clientele is based all the way from North America, and Europe, to Asia. Our 100+ software engineers have strong technical skills, think strategically, and work thoughtfully instead of just following specifications.
Several of our clients say they partner with us for our ability to work independently. Many have gotten used to our responsive, proactive, high-quality work, quick turnaround time, and on-time deliveries. This has led them to make us their partner of choice for any e-commerce implementation, customization, and maintenance assignments. Several of our clients have recommended us to their other business partners.
Navabrind IT Solutions is recognized for transparent processes, super responsiveness, cost-effective solutions, and deliveries within time and budget. Our customers say that our work most often exceeds their expectations.
You can partner with us for project-based services, sign up for a retainer, or engage with us on technology-specific assignments. Some clients also partner with us on duration-specific projects such as quarterly, half-yearly, or yearly. Irrespective of what you sign up for, we are deeply committed to maximizing your investment and ensuring your website is always secure.
Reach us to learn more about our expertise in implementing a Magento security scanner or to begin a conversation about your needs.
- Post
A Business Case for Hiring Dedicated Salesforce Developers
A Business Case for Hiring Dedicated Salesforce Developers March 21, 2025 Posted by: Tony Stark Categories: Blog, Hire a Developer, Odoo No Comments The Growing Need for Salesforce Development Services Salesforce has established itself as the world’s leading CRM, empowering businesses of all sizes to streamline customer interactions and improve sales processes. However, to experience - Post
ERP Migration from MS Dynamics 365 Business Central to Odoo
ERP Migration from MS Dynamics 365 Business Central to Odoo March 19, 2025 Posted by: adminuser Categories: Blog, ERP Migration, Odoo No Comments Migrating from Microsoft Dynamics 365 Business Central to Odoo ERP Solutions is a strategic move for businesses seeking flexibility, cost efficiency, and seamless integration. While MS Dynamics is a powerful ERP, many
How can we help you?
Get in touch with a solutions consultant that can share best practices and help solve specific challenges.